The most powerful hacking phones available
Customized Hacking Phones for Red Teamers, Pentesters & Ethical Hackers

What we do – a 3 step process
Get Yours Now
Choose a Phone and Customization Options
Choose a phone from Samsung, Google, Nubia or OnePlus, choose your ROM and other customization options.
We Build To Your Chosen Specifications
We do all the heavy lifting, installing & setting up the software, configuration and customization for you.
You Receive Your Phone within 21 days*
Phones are typically received worldwide within 21 days. This can be faster with premium shipping options.
Featuring: Over 2200+ Tools in Kali | 2900+ Tools in Blackarch | 600+ Tools in Parrot | Plus thousands more
One Device 2 Pwn Them All
A red team exploitation powerhouse
The World’s Most Advanced Mobile Penetration Testing Platform
Every day carry
Ready when you are
From handshake to takeover
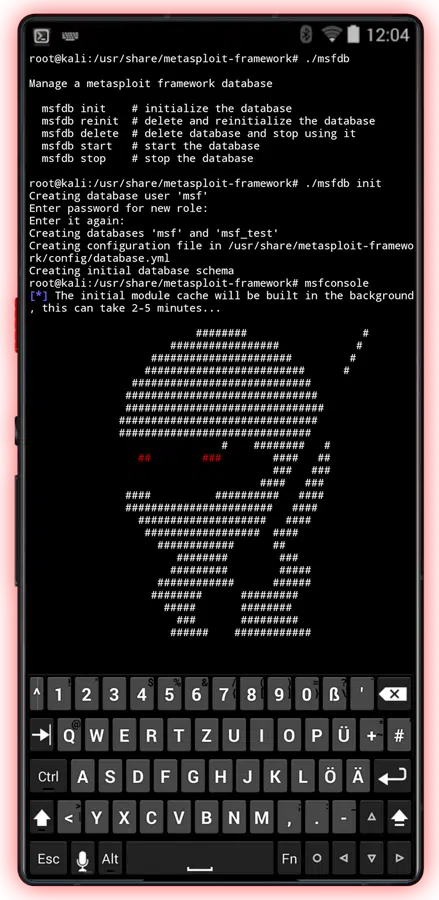
Their WiFi, Your Network
CYPH34PUNK phones don’t just give you access to WiFi networks—they let you break them apart, piece by piece. Deauthentication attacks? That’s just the beginning. Knock devices off the network like you’re flipping a switch. Force them to reconnect, only this time, they’re connecting to you, or rather your Evil Twin. Set up a fake access point that looks just like the real one, sit back, and capture everything — credentials, sensitive data, the whole show.
WPA/WPA2 handshake captures? This phone devours them. You don’t need to be in the same room. You don’t need their trust. You just need time. Grab the handshake, send it to your Hashcat GPU cluster in the cloud, and before you’ve even finished your coffee, the cracked password is back in your hands. The keys to the kingdom. Fast. Efficient. Silent.
But why stop there? With denial of Service attacks you could jam the entire network, flood the airwaves, and make sure nothing stays connected for more than a second. Total chaos. Or, you can set up your own rogue access point, manipulate the traffic as it comes through. Inject malicious packets, reroute them wherever you want, surveil every byte of data without leaving a trace. They’ll never know.
CYPH34PUNK phones let you do more than hack WiFi. They let you dominate it. You’re controlling the entire flow of information. It’s not about whether you can get in, it’s what you’ll do once you’re inside.

Something to get your BrakTooth into
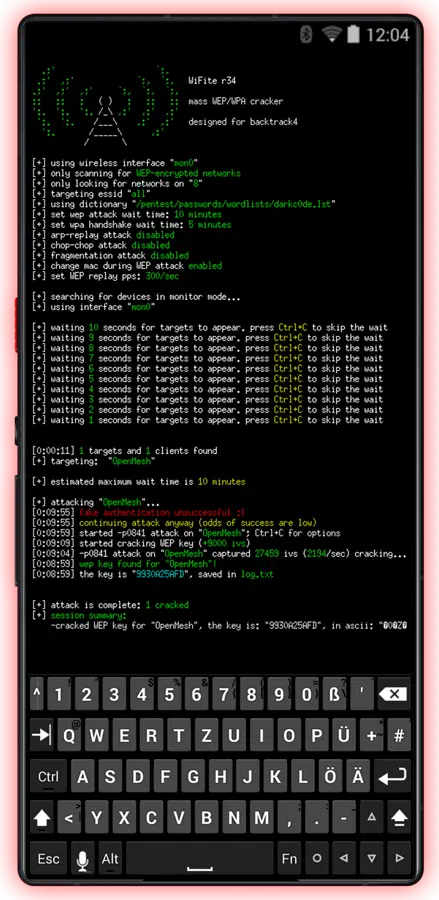
Bluetooth Systems Are Wide Open
For CYPH34PUNK phones Bluetooth isn’t a convenience — it’s a weak point, and you have the tools to tear it open. Corporate networks are littered with Bluetooth-enabled devices, from Bluetooth locks to wireless keyboards, and this phone can slip into their connections without ever raising an alarm.
Many devices still rely on insecure pairing methods and tools like BtleJuice let you perform Man-in-the-Middle (MitM) attacks during pairing, giving you the power to intercept, manipulate, or even take control of the communications. Wireless headset on the CEO’s desk? Now you can intercept confidential calls. Pairing isn’t a safeguard—it’s an entry point.
Range? No problem. Exploit connections from a quater mile away, intercepting signals from a secure BLE lock on a restricted server room, using KNOB to force devices to use weaker keys making them easier to crack, or manipulating a trusted connection to get the access you need — all from the comfort of your car parked in the lot.
Take this even further with the BIAS (Bluetooth Impersonation AttackS) flaw which allow you to impersonate a trusted device and infiltrate secure systems as if you were an insider. Tools like Spooftooph can clone Bluetooth identities, making the device you’re impersonating indistinguishable from the real one. It’s like walking into the office wearing the IT admin’s badge—you’re part of the system before anyone even realizes you’re there.
Bluetooth isn’t just wireless communication anymore — it’s a blind spot for most corporate security teams. With a CYPH34PUNK phone, you’re not just intercepting signals, you’re controlling them. From corporate boardrooms to restricted server rooms, Bluetooth becomes the pathway for red teamers to demonstrate how easily an organization’s defenses can be breached.
Bypassing the perimeter
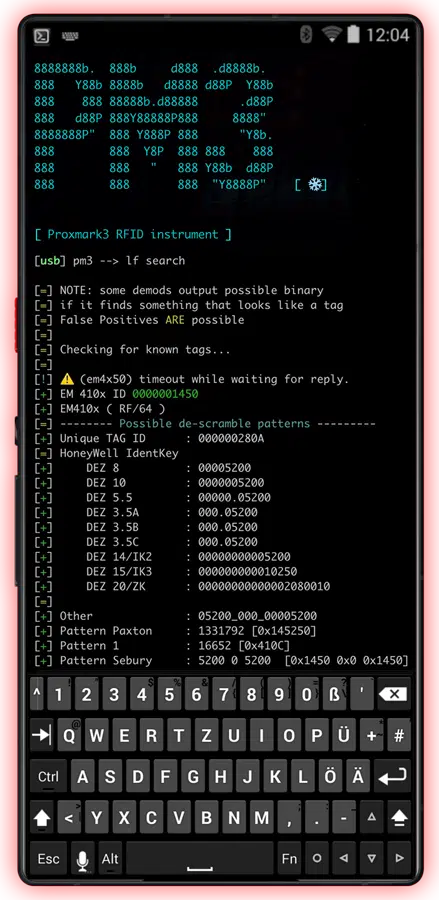
RFID Keys to the Kingdom
CYPH34PUNK phones take RFID hacking to the next level. A potent tool for breaching access controls and manipulating RFID systems. Most modern access control systems rely on RFID for entry, and with a CYPH34PUNK phone, you can capture the unique data from RFID tags, allowing you to create a duplicate in seconds. With this, you walk into secure areas as if you belong there. It’s not just duplication—it’s infiltration.
Imagine walking past a security checkpoint with the recorded credentials of an authorized user. It’s not just about getting through doors; it’s about doing so without ever needing the real card.
Sneak into conference rooms or secure areas by reading and writing NFC tags with ease. Corporate environments rely heavily on these technologies for security, making them prime targets for exploitation. With a CYPH34PUNK phone, you’re not just showing the vulnerabilities; you’re demonstrating how easily RFID systems can be compromised. Every card, every tag, every access point becomes a potential entry vector under your control.
CYPH34PUNK phones redefine what’s possible in RFID hacking. They turn an ordinary smartphone into a powerful tool for breaching the most secure environments, exposing weaknesses, and proving that no RFID system is truly secure until you say so.
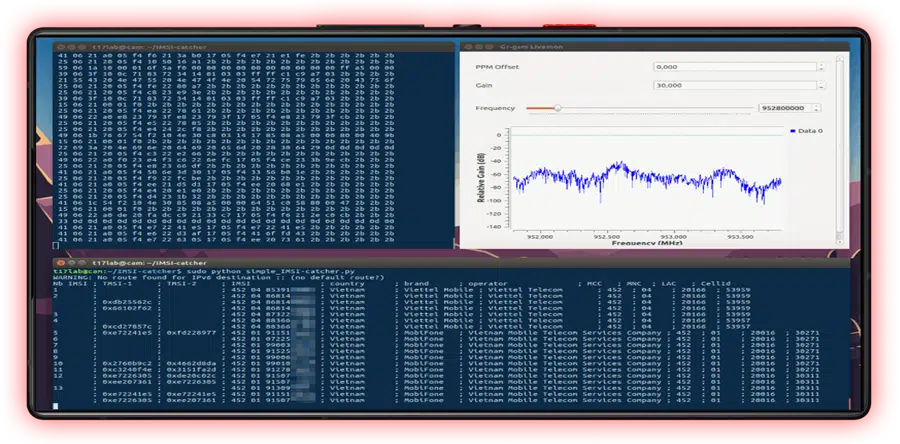
Phreak Frequency – an IMSI Catcher in the palm of your hand
Full Spectrum Radio Frequency Hacking
With CYPH34PUNK phones, Software-Defined Radio (SDR) hacking isn’t just a possibility — it’s a revolution. Turn your CYPH34PUNK phone into a powerful SDR station, allowing you to tap into and exploit the vast spectrum of radio frequencies that most people think are secure.
Imagine intercepting and analyzing signals with the ease of swiping through your apps. CYPH34PUNK phones give you the capability to listen to and manipulate signals from a multitude of wireless devices, from garage door openers, security gates and barriers, to industrial control systems. Every signal becomes an open book, revealing its secrets as you decode and replay its contents.
With this phone, you’re conducting sophisticated attacks, turning frequencies into a tool for disruption. Spoofing? It’s child’s play. By analyzing and mimicking the exact frequencies and protocols used by various devices, you can inject your own signals into a network. Pretend to be an authorized device, fool security systems, or manipulate communications with precision.
Reverse-engineering radio protocols becomes second nature. CYPH34PUNK phones let you decode complex communication protocols, exposing vulnerabilities in wireless systems. Once you have the blueprint of a protocol, exploiting its weaknesses is just a matter of applying the right signal manipulations.
The power to control radio communications is at your fingertips. Use your phone to disrupt, intercept, and manipulate the very frequencies that underpin modern communication systems. Each transmission is a potential target. You’re not just observing the signals—you’re redefining their purpose. Whether it’s neutralizing security measures or breaching otherwise protected systems, your phone is the ultimate device in a world where every frequency is a potential breach point.
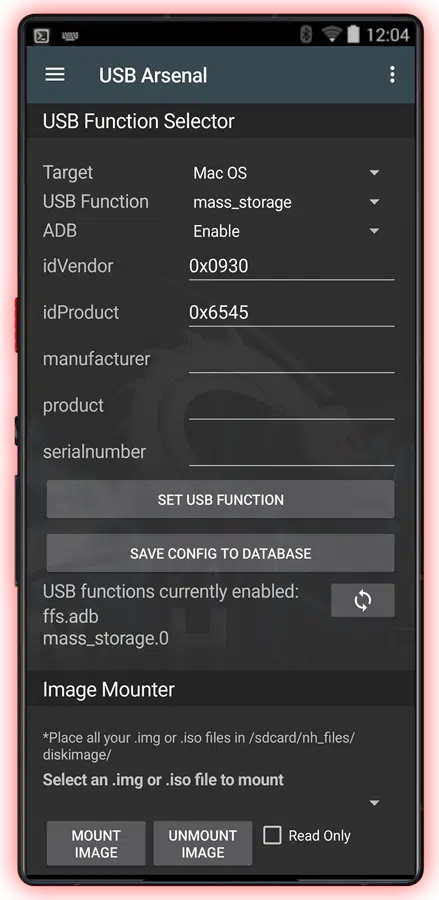
Access any computer
Bypass Login Screen Passwords in Seconds
CYPH34PUNK phones are not just gadgets—they’re precision instruments for dismantling security barriers across Windows, Mac, and Linux systems. These phones don’t just hack; they redefine what it means to bypass security protocols with unrivaled sophistication.
CYPH34PUNK phones go beyond exploiting vulnerabilities—they give you the power to bypass login screens entirely. You’re not guessing passwords; you’re walking right through them. On both Windows and Mac systems, this phone can seamlessly bypass password prompts during boot, granting you immediate access to a locked machine without even touching the credentials.
It doesn’t stop there. In minutes, you can reset OS passwords, modify system files, or straight-up exfiltrate data without leaving a trace. No brute force, no noise—just clean, direct access to everything behind that password wall. Imagine being able to wipe out the security layer of any machine, crack it wide open, and walk out with whatever you want, faster than a full system boot. CYPH34PUNK phones aren’t about fighting your way in—they’re about making the system open itself to you.
Intercept, redirect, misdirect
Man-in-the-Middle (MitM) Attacks
With a CYPH34PUNK phone you become more than just an observer, you have the power to position yourself right in the middle of any communication. You’re the gatekeeper, the manipulator, the one who decides what data flows through and what gets rewritten in transit. Tools like Ettercap and Bettercap aren’t just software; they’re your key to absolute control over the flow of information.
Intercepting communication between two devices is just the starting point. Their emails, logins, banking info—it’s all exposed. You’re not just watching the conversation happen; you’re making it happen on your terms. And the best part? They’ll never even know.
DNS spoofing and session hijacking lets you take things even further. Gain full control of their online accounts, email, social media, or anything else they’ve logged into. Once you’re in, you own their digital identity, with the ability to manipulate their interactions, harvest their data, or send out malicious links under their name.
These phones turn the concept of trust in digital communication into a joke. You’re not just in the middle of the conversation; you control the entire narrative. Data exfiltration, session manipulation, credential harvesting—it’s all possible, and it’s all in your hands. With a CYPH34PUNK phone, MitM isn’t a tactic. It’s your new way of life.
My battery is 1% and I need to send an emergency text, can I just plug into your laptop for a second, please?
BadUSB, Pwn & Control Remotely
Imagine the power of bypassing system security with nothing more than your phone. With a CYPH34PUNK phone, you’re equipped to exploit a multitude of known vulnerabilities and exploits in operating systems. This isn’t just about accessing a system; it’s about dismantling its defenses from the ground up.
Credential harvesting is just the beginning. Your phone can tap into a network, intercept login credentials, and crack passwords with ease. CYPH34PUNK phones leverage advanced techniques to siphon off authentication details directly, whether through passive sniffing or more aggressive methods.
Privilege escalation flaws are your playground. With CYPH34PUNK phones you can identify and exploit these weaknesses, allowing you to elevate your access from a basic user to an administrative powerhouse. Bypassing User Account Control (UAC) on Windows or exploiting sudo vulnerabilities on Linux becomes a seamless process. Gain root access, manipulate system files, and take control as if you were the system administrator all along.
Custom payload creation is where things get truly powerful. With the phone’s integration with tools like Metasploit or Empire, you can design and deploy bespoke payloads tailored to your needs. Whether you’re looking to establish remote access, deploy keyloggers, or exfiltrate sensitive data, CYPH34PUNK has you covered. Craft payloads that exploit unpatched systems or use social engineering tactics to trick users into compromising their own security.
This isn’t about brute force; it’s about finesse. Each vulnerability you exploit, every security protocol you bypass, is executed with precision. CYPH34PUNK phones turn your security bypassing efforts into an art form, making the act of breaking through defenses as effortless as swiping through your apps.
In a world where every system is a fortress, CYPH34PUNK phones are your keys. They don’t just open doors—they shatter them, turning high-level security into a minor inconvenience. Your phone becomes not just a tool, but an extension of your hacking prowess, capable of bypassing any barrier and taking control of any system.
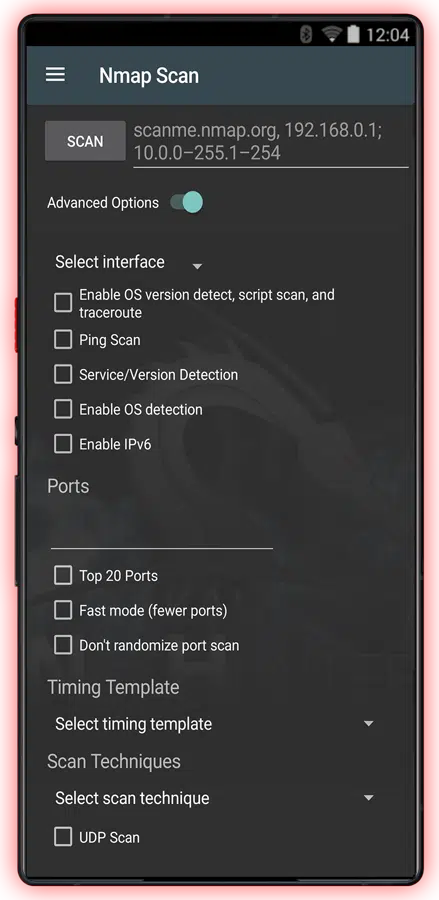
Find every device on the network
Network Scanning
CYPH34PUNK phones don’t just scan networks—they dissect them. It’s not just about running a few commands and collecting some basic info. This is about turning a network inside out, seeing every crack, every exposed nerve, and figuring out how to exploit everything. Nmap? Sure, that’s part of it. But Nmap is just the beginning. The real power comes when you start connecting the dots, piecing together a full map of every device, every open port, every service running, every vulnerability just waiting to be exploited.
With these phones, you’re not just scanning for open ports—you’re fingerprinting every device on the network. The phone identifies not just the services, but the exact version of the software running on them, flagging unpatched systems like it’s picking targets in a shooting gallery. Windows 7, 8 or 10? Easy target. Outdated Apache server? Open door. Unpatched SSH daemon? The key to the kingdom. It’s not just about seeing what’s there; it’s about knowing what can be broken.
But scanning is just phase one. CYPH34PUNK phones don’t just identify weak points—they give you a tactical advantage. Misconfigured firewalls that were supposed to keep the bad guys out? You walk through them like they’re not even there. You’ve got the tools to exploit the most vulnerable systems or services that the scan reveals. Network admins who think their systems are locked down have no idea how wrong they are.
Network scanning is more than just reconnaissance. It’s about taking control. It’s about building a complete picture of the network’s weak points and using that information to strike hard, fast, and precisely, all from a phone that fits in your pocket.
Why Us?
We’ve been building nethunter phones since the days of the Pwnie Express Pwn Phone which came out in 2014 and was featured in the hit hacker TV show Mr Robot in 2016. We’ve come a long way since then and now deliever the phone Elliot would use if there was a new up-to-date serise of the show. We make the most tactically advanced and highly customized hacker phones on the market.
